Resources

Blog & News

Adding a Streaming Gateway Appliance to Your Bring Your Own Azure Private Network
Adding a Streaming Gateway Appliance to Your Bring Your Own Azure Private Network

WRITTEN BY
TABLE OF CONTENT
IMPORTANT
We advise customers to create a separate Azure VNET to contain the Frame workloads. This allows customers to separate and isolate their Frame-related resources from their other Azure resources, allowing customers to report on and apply distinct (if required) security policies to the Frame resources or on the Frame VNET.
When creating a subnet(s) within your VNet for your Frame workloads, make sure that the CIDR block of the subnet is /18 or smaller (e.g., /21, /23, /24 etc.).
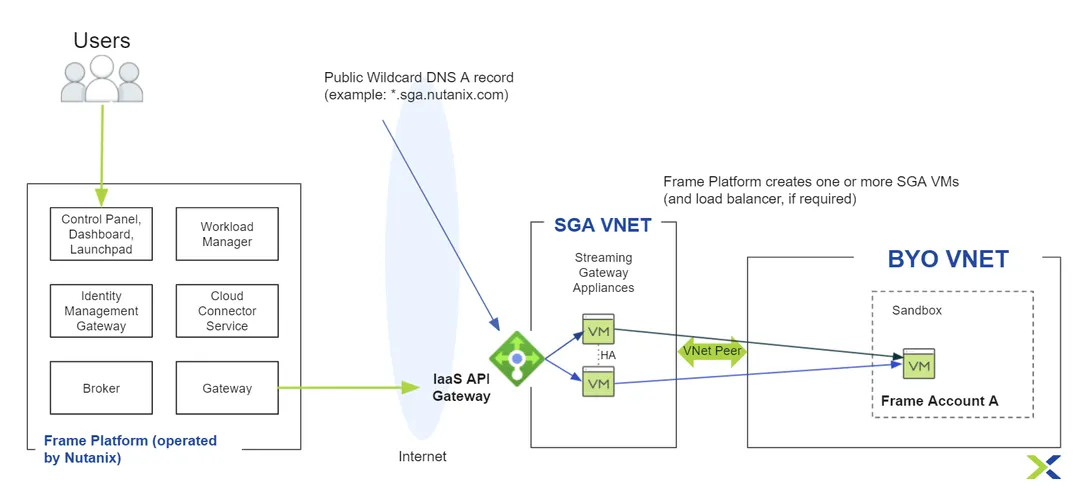
For customers who want their users to access these workloads from the Internet without a VPN, Nutanix provides the Frame Streaming Gateway Appliance (SGA), a secure reverse proxy that supports the Frame Remoting Protocol (FRP) 7 (Secure WebSocket-based) and 8 (WebRTC-based). The SGA allows you to securely grant users access to virtualized applications and/or desktops running in the Azure private VNet without a VPN.
In general, there are two ways to deploy SGAs: (1) manual creation where customers have control over the wildcard subdomain, SGA public IP address, DNS wildcard A record, and SSL certificate lifecycle; and (2) automated deployment where the Frame platform is responsible. In this blog, I am going to walk you through the process of deploying an SGA using the Frame auto-deploy SGA feature in the context of a BYO Azure private network.
Figure 1 below illustrates the architecture of what you will use in this scenario:
Requirements
For setting up Frame Account with Bring Your Own (BYO) Private Networking and using the SGA, you will need to:
- Deploy networking resources in your Azure subscription.
- Have a Frame customer or organization entity with a registered Azure subscription (instructions for attaching your Azure Subscription to your Frame customer or organization entity can be found here).
- Create the new Frame Account with BYO Networking.
- Request SGA auto-deployment from Frame Support.
Deploy networking resources in your Azure subscription
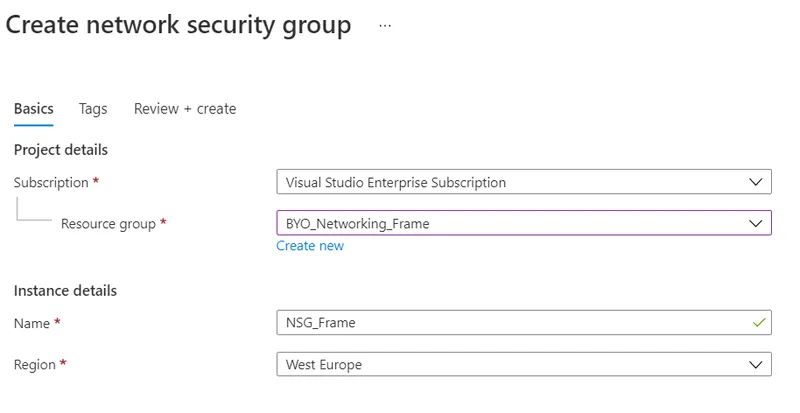
To create a Frame account in one of your existing customer-managed Azure VNets, you will need to set up a new Resource Group (RG), Virtual Network (VNet) with one or more subnets, Network Security Group (NSG), and connect that NSG to subnet(s).
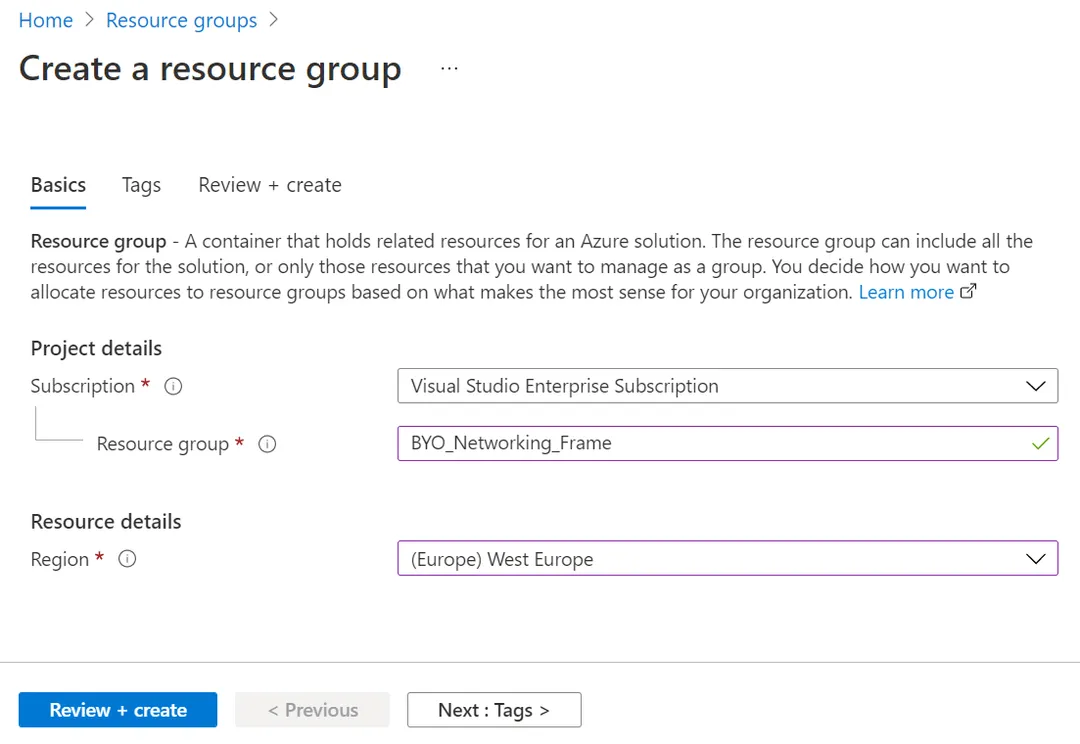
RG creation
A resource group is a container that holds related resources for an Azure solution. In our case, we will create RG in West Europe to hold network resources as seen in Figure 2.
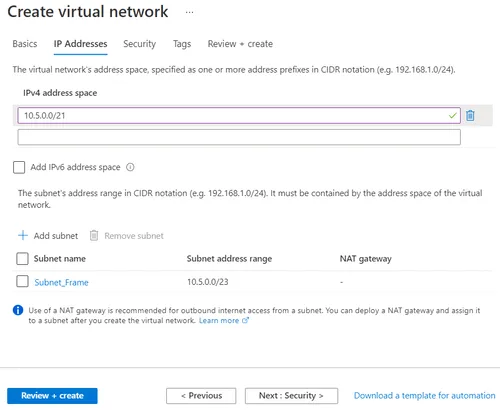
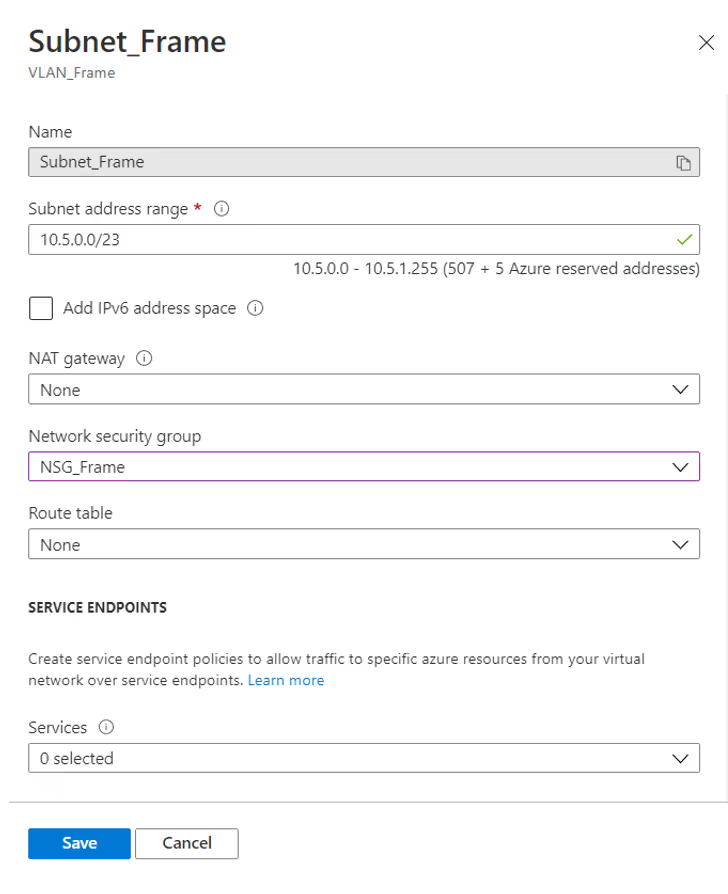
VNet and subnet(s) creation
Then, you should create a virtual network in that resource group with one or more subnets, depending on how many Frame accounts you want to have. In Figure 3 below, I created a VNet with a /21 and put a subnet that is /23 inside.
NSG creation and connecting NSG with workload subnet(s)
Now is the time to create a network security group and attach it to the subnet(s) that will contain the workloads. In Figure 4. I'm creating a NSG with default in-bound and out-bound rules. In Figure 5. I'm attaching that NSG to the Frame-workload subnet.
Create the new Frame account
Once the Azure VNet is configured, I can proceed with the creation of my Frame account, which will be contained in the Azure VNet.
Note: I have already registered my Azure subscription to my Frame organization entity (as noted in Prerequisites #2).
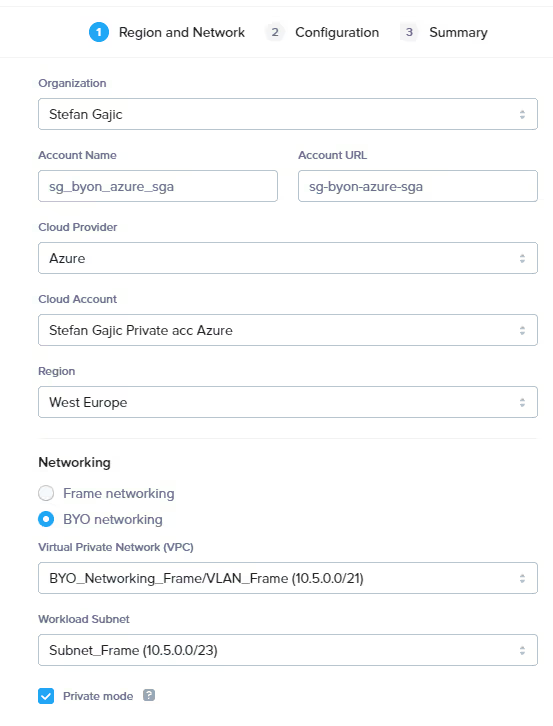
In the "Create Account Dialog," I choose the correct cloud provider "Azure." For the region, I chose "West Europe" as I created the Azure resources in that region. Then, I select the "BYO Networking" radio button, as seen below.
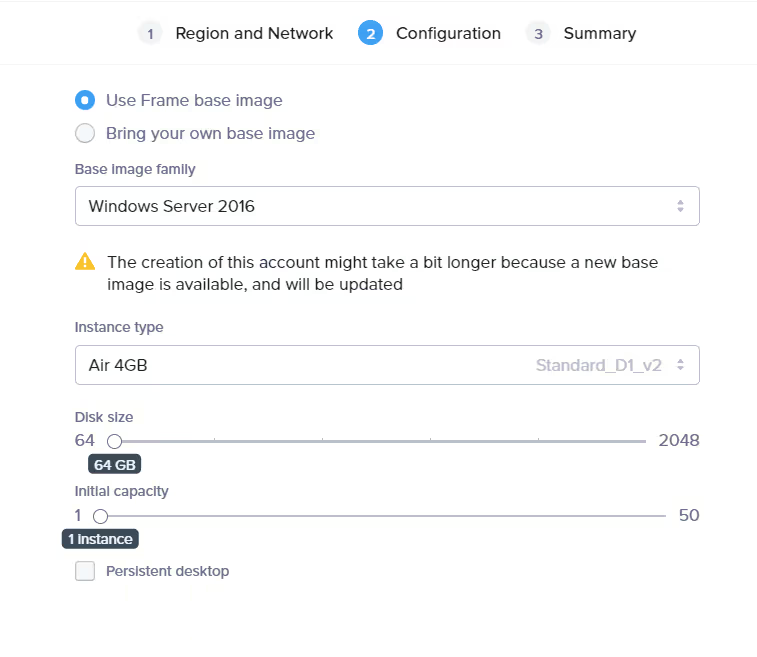
I chose the Virtual Network and subnet that I have created, and now I can select my sandbox image and instance type and hit "Next" twice to create my Frame account.
Once the Frame Account creation is finalized, you will notice that a resource group (RG) named azr-prod-v{vendor_id}-instances-{incrementing_index} is created in your subscription. In this RG, you will find your Sandbox VM and other Frame workload VMs based on the capacity you specify.
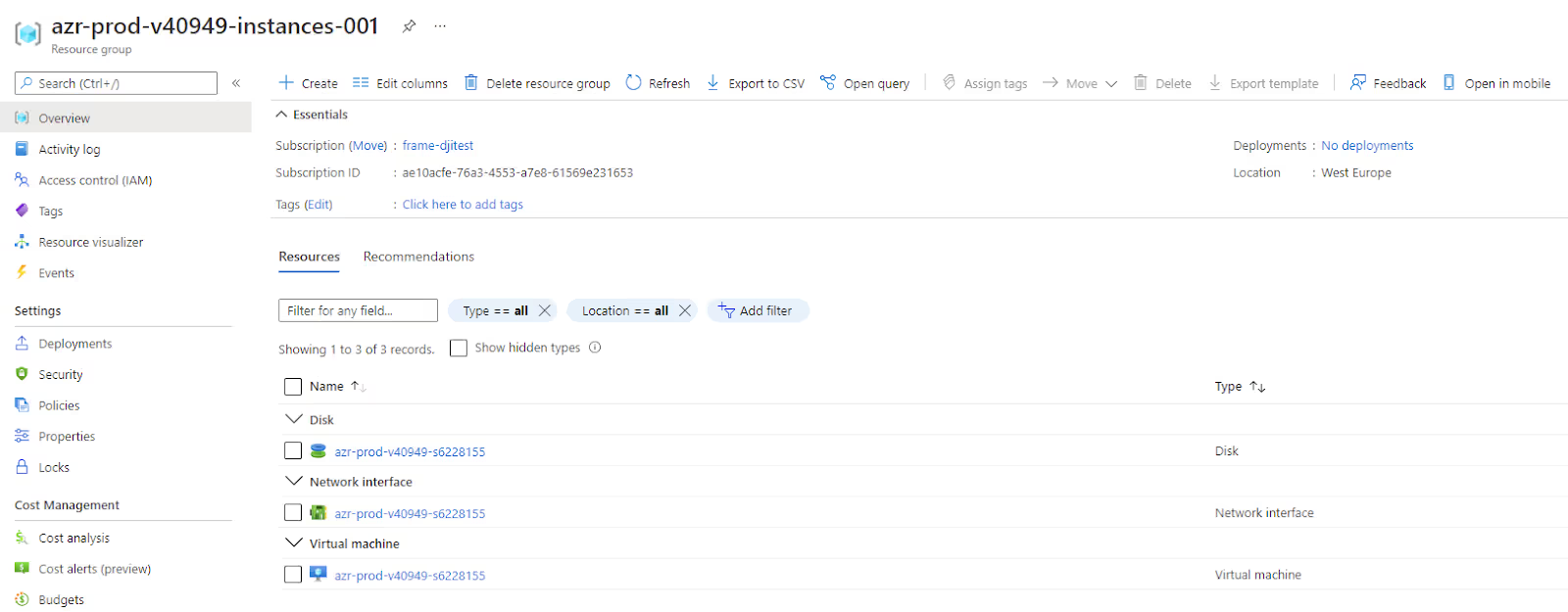
Please notice that the VMs will have only private IP addresses and will be accessible only from the internal network. In order to make them accessible from the internet, you will need to submit a request for SGA.
Request for SGA
Congratulations! Your technical part of the job is now done, and you have a Frame account with its workloads in your specified VNet/subnet. Now, let Frame support do its magic and create SGA resources under your subscription in an adjacent VNet.
To request the auto-deploy of one or more SGA VMs, please go to https://my.nutanix.com, log in with your credentials, and submit a support request by launching the Support Portal.
The form will look like shown in Figure 10 below.
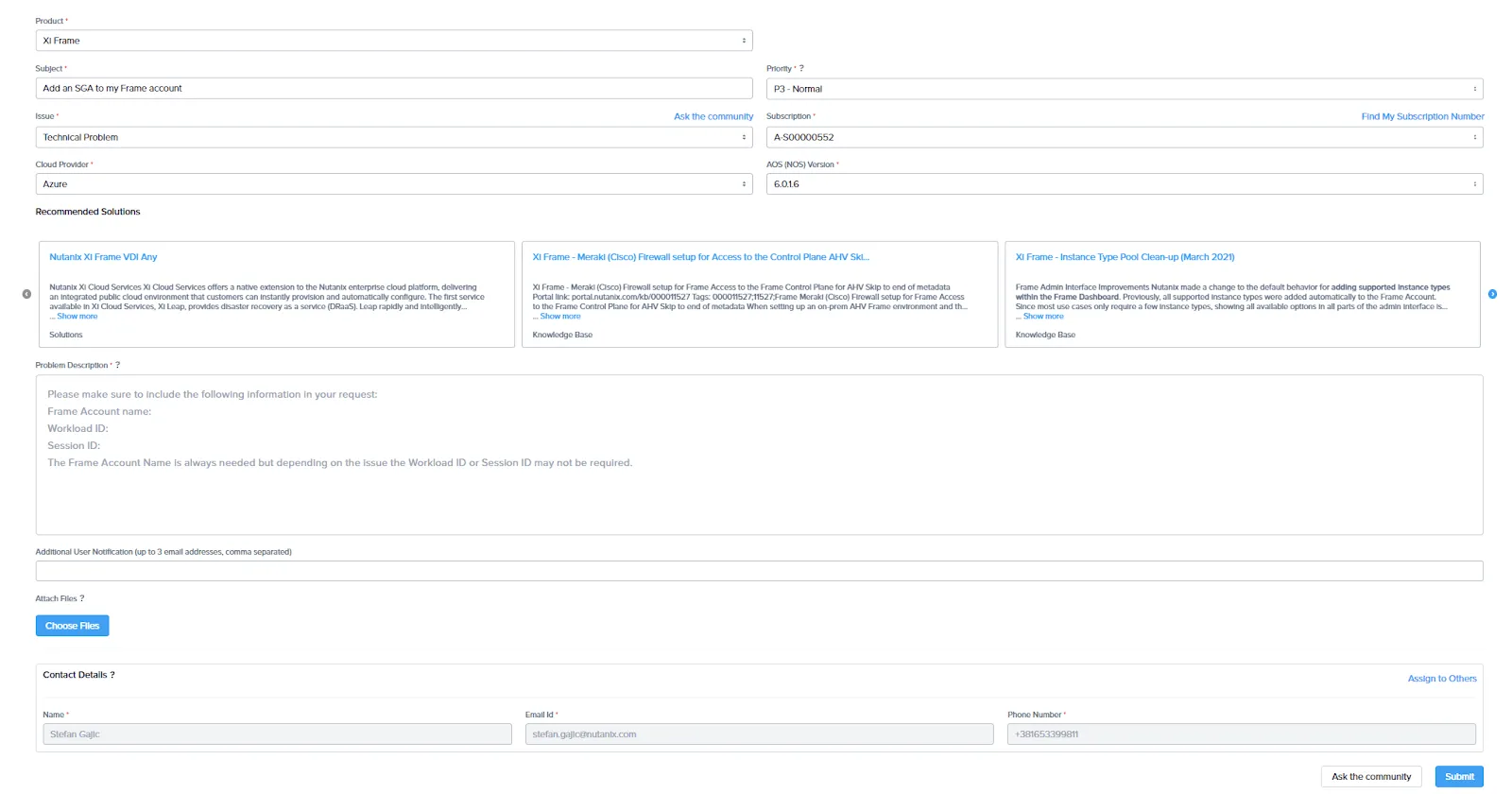
Specify the following information in the support request form:
- Product: Nutanix Frame
- Subject: "Add an SGA to my Frame account"
- Issue: Technical Problem
- Cloud Provider: Azure
- Priority: P3-Normal
- Subscription: Your subscription
- AOS (NOS) Version: Not relevant and can be set to the latest version
- Problem Description: Enter the following details:
- Customer name: e.g., Nutanix-Demo
- Organization name: e.g., Nutanix-Demo-Org01
- Name of account or accounts that you want to connect to SGA(s): e.g., Nutanix-Demo-Acc01
- Frame workload VNet CIDR and subnets CIDR (must be /18 to /24): e.g., 10.5.0.0/24
- Automatically use the SGA for existing and future Frame accounts in the specified VNet/subnet? e.g., Yes: configure all existing and future accounts to use SGA or No: configure only this specific account to use the SGA
- Number of SGAs to be created (1 or more): e.g., 1
- SGA VNet CIDR (/24 or /26 is required): e.g., 192.168.1.0/24
Please make sure that SGA VNet CIDR is not overlapping with Frame-workloads VNet CIDR. By default, Frame will use 172.16.0.0/24 for SGA VNet. If more than one SGA is requested, then an Azure Load Balancer will be provisioned in front of your SGA VMs.
Azure Resources Provisioned
Once the process of SGA enablement is done, you will see the following resource group in your Azure subscription, as shown in Figure 11.
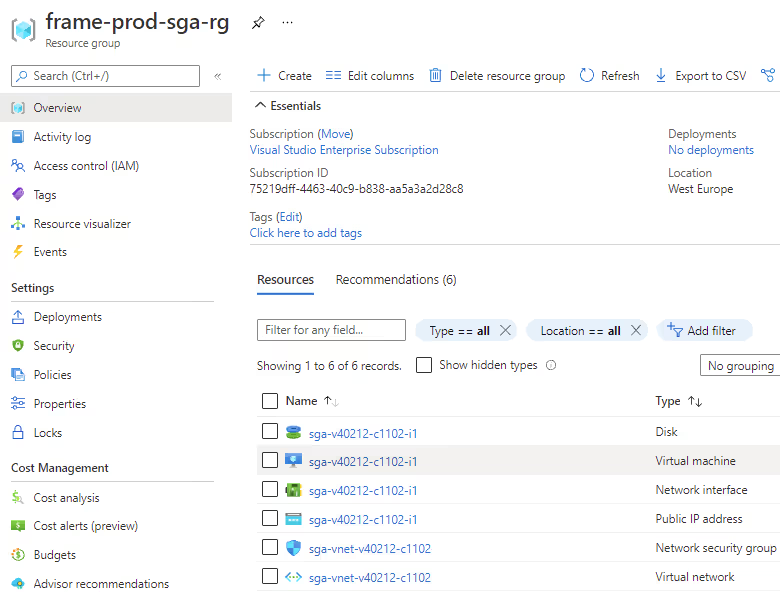
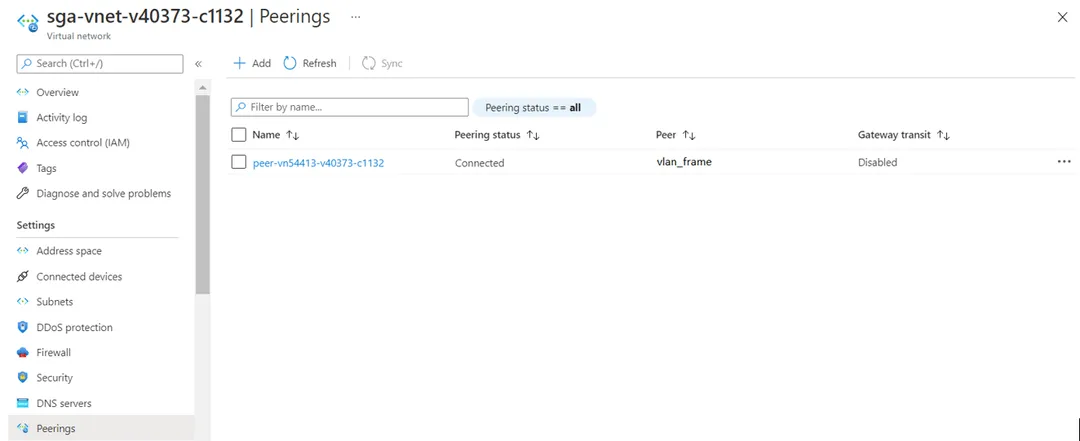
If you requested one or multiple Frame accounts in the same VNet, peering between the SGA VNet and the Frame workload VNet is done automatically by the Frame platform, as shown below in Figure 12.
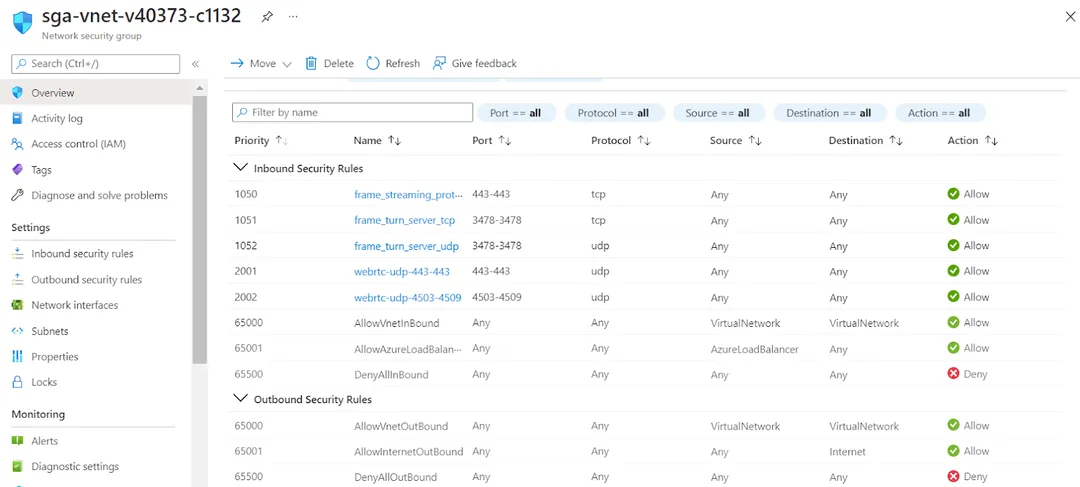
Frame will create and configure your NSG to allow only mandatory inbound traffic.
If you wish to have multiple Frame accounts in different VNets, please expect notification from our support team to create the VNet peer(s) between the SGA VNet and the remaining Frame workload VNets on your own. Note that the remaining Frame workload VNets must have CIDRs that fall within the Frame Workload VNet CIDR specified in the support ticket.
Conclusion
In this blog, we showed how you could set up a BYON Frame account in Azure and use Streaming Gateway Appliance for secured connection between the end user and the workload VM without need of VPN. The workloads of the Frame account will only have private IP addresses on your private network; therefore, they inherit all the existing network security controls that would be set up on your private network. Users will be directed for that Frame account to the public IP address of the SGA (or the Azure Load Balancer for two or more SGA VMs) to reach the workload VMs.

